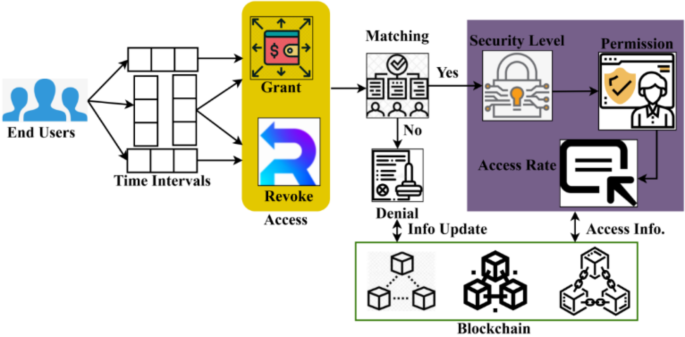
System architecture
IoT-based healthcare systems utilize service forwarding to the appropriate patient. This deployment of an IoT environment enables ubiquitous and convenient patient access to related services. The ubiquitous data is stored in an authorized repository to determine access to secure users. In the healthcare industry, IoT detects the data; based on this, the service is provided on time. The computation time is decreased, and the patients handle the relevant information. The storing of relevant and irrelevant data is done on the repository; from this approach, the access level states the user’s health. This study proposes a fully decentralized authentication strategy leveraging blockchain to address the shortcomings of the present centralized authentication solutions. A distributed network of computing devices powers a blockchain called nodes.
Using the term opportunistic suggests that the proposed system may prioritize adaptability and flexibility in access domains, potentially by introducing some level of false positives or false negatives in certain situations. Such a metric is analyzed to accommodate dynamic or changing conditions and adapt to them. Incorporating blockchain technology is part of an effort to enhance transparency, traceability, and accountability in access decisions.
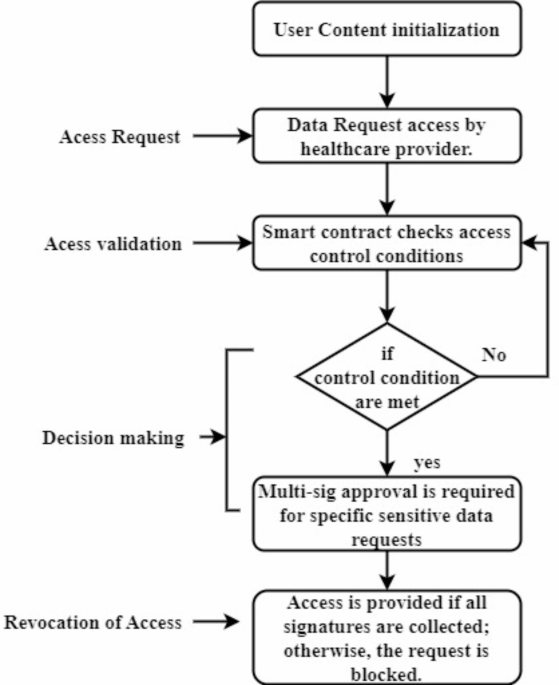
Every node keeps an archive of blockchain technology containing encrypted data on patient records. Thanks to this decentralized storage, data availability is improved as there is no single point of failure. Blockchain creates a safe ACM using cryptographic methods. Smart contracts, autonomous, rule-based contracts, can control who has access to patient records. Only parties with permission to see or alter the patient data can do so, thanks to smart contracts’ enforcement of access control restrictions. The proposed scheme’s process is illustrated in Fig. 2.
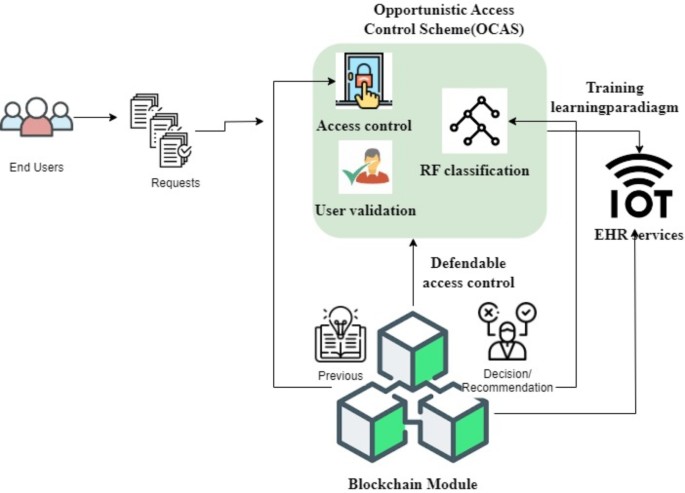
The proposed Opportunistic Access Control Scheme.
The proposed scheme performs user validation, access control, and decision-making using the blockchain paradigm. The assessment is based on the previous user information, such as access and revocation. Based on this information, blockchain provides users with access to delegations. User validation relies on identity verification and denial history (Fig. 2). The order or sequence in which permissions for access are assigned to various individuals inside a system is called the delegation sequence. According to historical data and user requirements, the delegation sequence enables the system to keep track of access privileges and make educated judgments about giving or denying access. Data security is ensured for the number of services and determines the relevant processing. The relevant service is evaluated for the access control scheme. The user permission is used to delegate the defendable access control scheme. The authorized repository defines the concord patient in the healthcare industry. All nodes on the blockchain network will not have a backup of the data once it is put in the blockchain because the technology is not tamper-proof. The security and privacy of medical records are considerably enhanced if an attacker interferes with the data in some nodes since the erroneous data will be found and corrected by other nodes.
Healthcare IoT data access management is the goal of the OACS, which combines machine learning for adaptive decision-making with blockchain for secure access control. At its heart, the OACS is a distributed ledger system that records all transactions, including those involving access requests (approved or denied). Smart contracts automate the process of enforcing policies related to access control. With each access request, the smart contract verifies the user’s identity and verifies the data permissions and predefined restrictions. Because these smart contracts are unchangeable once deployed, they add another safeguard by ensuring the rules for access control are consistent and trustworthy.
Along with blockchain technology, the OACS also uses RF techniques for machine learning to assess access requests. The system utilises considerations such as user role, data sensitivity, access context, frequency of prior accesses, and request geolocation for classification. Access requests are categorized as valid or suspicious based on these factors. The system may adjust to its users’ evolving demands and behaviours by processing past data using the RF algorithm. One way the algorithm can help prevent unauthorized access is by detecting suspicious patterns of requests (such as those coming from an unexpected location) and then implementing extra authentication processes.
The OACS takes the following steps in response to an access request:
(1)
An initial step in the validation process is for the system to compare the user’s credentials and previous actions with those stored on the blockchain.
(2)
The OACS checks the blockchain for their delegation history, including previous attempts, permissions, and revocations, to verify that the user has the right authorisation for the resource they are requesting.
(3)
For the final decision, the RF algorithm looks at the request through the lens of past access trends and behavioural analysis. This assessment determines whether the request is approved or denied by the OACS.
(4)
After reaching a decision, it is added to the blockchain as a new transaction, ensuring that the access request record cannot be altered.
Utilizing methods like sharding to divide the blockchain and reduce processing costs for each node and off-chain storage for non-critical data, the OACS tackles possible scalability difficulties, especially in high-traffic IoT applications. This makes it ideal for widespread healthcare IoT deployments since it keeps the system responsive even under heavy strain.
Unauthorized people can attempt to get physical access to IoT devices that support them. To do this, one can tamper with the devices, directly extract data from memory, or connect to the network to intercept or modify data transfers. The access level is kept secure by blocking unauthorized entrances and data downloads. Data security is guaranteed for various services, and the appropriate processing is chosen. The pertinent service is assessed in light of the access control plan. The defendable access control scheme is delegated via user authorization. In the healthcare sector, the authorized repository specifies the concord patient. The examples are: Blockchain offers a tamper-proof and unchangeable storage solution for medical documents called an authorized repository. Here, blockchain can store patient data, ensuring that once the information is recorded, it cannot be changed without the network’s participants’ consent. It preserves data integrity and stops unidentified people from tampering with the records. Blockchain relies on decentralized consensus methods, in which several network users verify and concur on the blockchain’s current state. With the help of this consensus model, healthcare records are protected against unilateral modification or manipulation, increasing the security against unauthorized access.
Here, similar information matches the current and the previous state and examines the authorized repository. The data repository provides access grants to the patient and maintains security. Blockchain is a ledger that includes healthcare data collection and provides similar information to the end-users. To determine the legitimacy of a healthcare provider’s access to patient records during an emergency, Eq. (1) represents the circumstances when access requests are being considered. User credentials, historical access patterns, and data sensitivity are defined; they are used to improve the healthcare IoT system’s security by re-evaluating permissions when an anomaly in access patterns is detected.
$$\:\gamma\:=\left(\frac{1}{{e}_{n}+{u}_{n}}\right)*{\sum\:}_{{g}_{r}}^{{e}_{0}}\left({m}_{i}+{r}_{0}\right)*\left(\left(\frac{\raisebox{1ex}{${r}_{d}\left({q}_{e}\right)$}\!\left/\:\!\raisebox{-1ex}{${e}_{n}$}\right.}{{w}_{0}+{t}^{{\prime\:}}}\right)+\left({k}_{h}*{m}_{i}\right)\right)+{j}_{c}$$
(1)
As shown in Eq. (1), where \(\:{e}_{n}\) denotes the number of active entities, \(\:{u}_{n}\) is the number of unauthorized users,\(\:\:{e}_{0}\) denotes the number of evaluated requests, \(\:{m}_{i}\)represents the access request metric,\(\:\:{r}_{0}\) denotes the constant factor related to an access request,\(\:{\:\text{q}}_{\text{e}}\) denotes user request,\(\:{\:\text{k}}_{\text{h}}\) indicates blockchain-based healthcare services, \(\:{\upgamma\:}\) represents anonymous entries,\(\:{\:\text{g}}_{\text{r}}\) signifies access grant, \(\:{\:r}_{d}\) symbolizes healthcare record holds, \(\:{w}_{0}\)is the information Forwarded to the appropriate user, \(\:{\:f}_{d}\) implies defendable services, \(\:{\:j}_{c}\) denotes record forwarding. The anonymous entries and data download define the access level for the number of services. Here, the computation determines the repository and examines the related services on time. An access control scheme for security analysis is employed, and it is stored in an authorized contract with a blockchain by identifying the user request and access grant for the initiated transaction flow was stored in a current state and then based on delegation knowledge and identifies the anonymity user request and then revoke it. Assuring consensus and preventing unauthorized changes, the distributed network of blockchain nodes collectively maintains the ledger and authenticates transactions. Security analysis was performed using the abovementioned procedures.
The computation process utilizes the recent IoT for ubiquitous and concord patients/users. A similar service is forwarded to the end-user by defining anonymity in the network. In IoT, the repository stores the collection of information and leverages the access level for security. The security level is maintained for anonymous entries and data downloads. For every iteration step, the analysis is carried out for the anonymous entries and data download.
The system manages access grants using blockchain technology. Based on prior access and delegation sequences, access grants are determined from blockchain records and can be revoked. The service handling deploys the augmentation and evaluation to refer to the access allowed to the end-users and is used to decide the blockchain. The requirement is assessed here, and blockchain provides security using Eq. (3). The decision is made for the deployable blockchain security and defendable access control followed by the security, and it is referred to in Eq. (4). This RF classification tree is used to classify the access, give and revoke suggestions given by blockchain, and forward the information on time. Equation (6) is used by the blockchain suggestion to analyze this scheme’s training stage of processing data and investigates the blockchain recommendation’s access-level security to ensure security. The security setting is appropriate for the range of services and widespread information sharing by accessing Eq. (13).
The detection process states the authorized service and forwards it to the defendable access control. This paper introduces an OACS for leveraging access-level security and the defendable access control scheme. The access-control scheme determines the related services, provides the authorized repository, and deploys ubiquitous information. The information forwarding is used to determine the healthcare record and estimate the defendable service to the end-users. Blockchain for the healthcare system is used to utilize the related services, and it is represented as\(\:{\:k}_{h}\). The number of users who request the requirement\(\:{\:q}_{e}\) in Eq. (2a) to the healthcare centre, \(\:\{{u}_{0},{u}_{1},\dots\:{u}_{n}\}\) and services are defined as\(\:\:\{{e}_{0},{e}_{1},\dots\:{e}_{n}\}\).
Here, analysis defines the anonymous entries to access the authorized record from IoT, referred to as\(\:\:\gamma\:\). The access is granted to the end-users based on the relevant information, and it is denoted as\(\:{\:g}_{r}\) described using Eq. (2b). The healthcare centre handles the requests/requirements of the patients\(\:{\:p}^{t}\), and matching is performed with the current and previous state, which provides the result. Here, the permission\(\:{\:m}_{i}\) is granted to the patient to ensure the security level. The healthcare record holds the collection of information regarding the patients, and it is represented as\(\:{\:r}_{d}\). In this approach, access control is used to determine the defendable services, and it is denoted as\(\:{\:f}_{d}\). The access control defines the blockchain for better record forwarding, and it is termed as\(\:{\:j}_{c}\). Thus, the information \(\:{\:w}_{0}\:\)is forwarded to the appropriate user on time\(\:\:{i}_{0}\). From this analysis approach, the examination for access level is formulated in the following Eq. (2). This equation calculates the access efficacy score (α), which indicates the likelihood of approval based on several parameters. Credentials, request significance, prior access trends, and present request context are considered. The score helps improve decision-making by revealing the access request’s legitimacy.
$$\:\alpha\:=\left({u}_{0}+{m}_{i}\right)*\left(\frac{H+{c}_{r}}{\prod\:_{{g}_{r}}\left(S*{r}_{d}\right)}\right)+\left({q}_{e}*{u}_{0}\right)$$
(2)
Query effectiveness (\(\:{q}_{e}\)) measures access request efficacy based on the time and resources involved. This equation considers timing, resource sensitivity, and other criteria to decide if an access request is appropriate.
$$\:{{q}_{e}=t}^{{\prime\:}}*{w}_{0}({g}_{r}+{o}_{n})$$
(2a)
This equation estimates the group of resources (\(\:{g}_{r}\)) associated with the access request by including data sensitivity (\(\:{f}_{d}\)), present request context (\(\:{c}_{r}\)), and access request metric (\(\:{m}_{i}\)). Quantification helps prioritize access requests by resource utilization to handle sensitive data correctly.
$$\:{g}_{r}=\left({f}_{d}+{c}_{r}\right)*{m}_{i}$$
(2b)
This equation evaluates the request context (\(\:{c}_{r}\)) using query effectiveness (\(\:{q}_{e}\)), a historical adjustment factor (\(\:{k}_{h}\)), and any necessary deviation or adjustment (\(\:d{\prime\:}\)). This equation uses the request’s context to determine if access is good in the current situation.
$$\:{c}_{r}=\left({q}_{e}+{k}_{h}\right)-d{\prime\:}$$
(2c)
In Eq. (2), the access level states the anonymous entries and data download. Here, the examination provides the authorization and deploys the security. The access control determines the defendable permission and examines the blockchain. The requirement provides IoT security augmentation and assessment for healthcare record access. The augmentation determines the access grant and provides the requirement, and it is represented as\(\:\:\left(\frac{H+{c}_{r}}{\prod\:_{{g}_{r}}\left(S*{r}_{d}\right)}\right)\).
Here, the requirement defines anonymous and data download and estimates the defendable access control. The assessment determines permission access for the requested users. The request is granted based on the healthcare record and deploys the authorization\(\:\:H\) for the user service handling. The service handling is examined to determine the appropriate information exchange between the users in IoT. Here, examination \(\:\alpha\:\) is performed for the requirement, and permission is granted to the users based on the anonymous\(\:{\:o}_{n}\) detection. The control is provided to forward the appropriate data to the end users, and it is represented as\(\:{\:c}_{r}\) and calculated using Eq. (2c). Figure 3 presents the user access grant procedure.
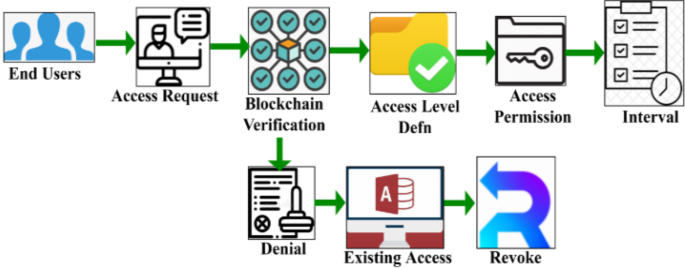
This access grant procedure is defined by two conditions, namely verification success and failure. Access level and user delegations are defined based on the available information. A failed verification (user) is revoked of current access, and the new request is denied (refer to Fig. 3). Blockchain security states the augmentation and assessment and defines the access grant. Thus, the data is forwarded to the users based on relevance, and it is represented as\(\:\:t{\prime\:}\). The defendable access control transfers the information to the appropriate user, and it is denoted as\(\:{\:f}_{d}\). The delegate service is handled by the end-users, and it is based on the access control and is denoted as\(\:\:d{\prime\:}\). Equation (3) performs the data forwarding based on the requirement and data delegated for defendable access control. From the access-level approach, an OACS is used for security maintenance and examines the user permission for the requirement for the data. IoT security is used to define the user permission delegated for service forwarding.
The defendable access control scheme defines the user permission delegated based on the requirement and data. The anonymous entries and data downloads are used to estimate the access to the secure users. The service handling is used to determine the blockchain and deploys the augmentation and assessment to refer to the access\(\:\:S\) granted to the end-users. Here, the evaluation is carried out for the requirement, and the blockchain is deployed for security.
Several aspects of forwarding processes require mathematical formulae by accounting for the parameters like user request on time for a particular requirement is verified by authorization and permission given for authorized users to access the information in the secured environment as represented in Eq. (3):
$$\:{f}_{d}\left({\varnothing}\right)={\prod\:}_{{m}_{i}}^{{u}_{0}}\left({w}_{0}+S\right)*\left(Y+\frac{H}{{c}_{r}}\right)-\left(\left({t}^{{\prime\:}}*{k}_{h}\right)*\:\:\left({q}_{e}-{i}_{0}\right)\right)+d{\prime\:}$$
(3)
The defendable access control \(\:{f}_{d}\) is calculated in response to blockchain security \(\:{\varnothing}\) by analyzing the authorization \(\:H\) the information \(\:{w}_{0}\) is forwarded on time \(\:{i}_{0}\) only when the permission\(\:{\:m}_{i}\) is granted to the patient \(\:{u}_{0}\) to ensure the security level and the blockchain augmentation to refer to the access\(\:\:S\) granted to the end-users. Considering the blockchain for the healthcare system to utilize the related services, it is represented as\(\:{\:k}_{h}\) the data is forwarded to the users based on relevance, and it is represented as\(\:\:t{\prime\:}\). User requirement request is given as \(\:{q}_{e}\) followed by analyzing the delegated service, which is handled by the end-users; it is based on access control and is denoted as\(\:\:d{\prime\:}\).
Access is granted to the secure\(\:\:Y\) transmission of data from one end to the other. The anonymous detection is detected, and the secure transmission is deployed for the requested user. The determination is done for the defendable access control and deployment of blockchain security, which is termed as\(\:\:\varnothing\:\). The computation is performed for the requirement, and it is based on the time, and it is formulated as\(\:\:\left(\left({t}^{{\prime\:}}*{k}_{h}\right)*\left({q}_{e}-{i}_{0}\right)\right)\). Thus, the delegation, requirement, and data forwarding are examined in Eq. (3), and the security is provided using Eq. (4).
$$\:Y=\frac{1}{{e}_{n}}*\sum\:_{{w}_{0}}\left(\left({c}_{r}+H\right)*\left(\gamma\:+\frac{{k}_{h}*{l}_{a}}{{m}_{i}}\right)\right)+\left({q}_{e}*{r}_{d}\right)-{\varnothing}$$
(4)
The security is maintained to prevent anonymous entries and data downloads, and the blockchain is deployed for assessment and augmentation. The computation is based on the access grant and provides the recommendation approach. The recommendation is performed for the healthcare record and states the access control for the number of services and users in IoT. The OACS is used in the healthcare blockchain and permits delegated service handling. The defendable service provides permission for the access control level and estimates the security. For the iteration step, the healthcare record is used to state the augmentation for the assessment and provide security. Security is ensured for the blockchain to handle the record.
Blockchain is used to refer to the augmentation approach for the access grant\(\:{\:l}_{a}\) to the number of users in IoT. The examination states the access grant by providing permission, and it is represented as\(\:\:\left(\gamma\:+\frac{{k}_{h}*{l}_{a}}{{m}_{i}}\right)\). Thus, the security level is balanced throughout the computation step for the number of services. Machine learning techniques such as RF can be used to determine access grants and revoke them based on the blockchain.
Random forest classification technique
IoT-based healthcare systems employ RF because they excel with mixed numerical categorical and high-dimensional data, making them suitable for flexible user access demands. In environments with frequent user behaviour changes, ensemble learning reduces over fitting. Feature relevance metrics from RF help us understand access choice criteria.
To train the data, it is necessary to gather access logs from the healthcare IoT environment, which record both authorized and unauthorized attempts to enter the system. Next, the dataset is prepared to deal with missing values and normalize features. Then, it is separated into training and testing sets to evaluate the model on unseen data. The classifier is trained to generalize and make correct predictions on future requests by learning patterns associated with successful access requests using the RF method.
Feature selection
Information like user role, data sensitivity, historical access habits, and contextual factors like time and place are key to access control decisions. Features are selected to detect these factors. Both recursive feature removal and the RF model’s feature relevance ranking reduce the number of features that affect classifier prediction performance. This keeps the model efficient and understandable without over fitting.
Optimisation of classifier parameters
Parameter tuning adjusts the RF classifier’s hyper parameters, including the number of trees, maximum depth, and minimum samples for splitting nodes. To ensure the model works optimally on the validation set, grid search and cross-validation are used to evaluate parameter combinations. The security framework’s effectiveness improves by tweaking the classifier’s distinction between allowed and unauthorized access attempts.
The OACS uses RF because it handles high-dimensional data well and prevents overfitting with ensemble learning. RF’s many decision trees improve anticipated performance and provide reliable access request evaluations. This precision is essential for real-time access control in IoT contexts because it permits quick and informed user rights decisions based on context and behaviour. The system’s capacity to quickly process massive datasets ensures low latency and adaptability, essential for meeting healthcare applications’ evolving needs.
Here, the computation states the blockchain for security. The permission is granted to the requested user and deploys the augmentation and assessment for the varying services. The security level is performed for the defendable service forwarding concerning requirements and data. The access grant and revocation are classified from this RF tree. Equation (5) considers many parameters to determine access control decisions (\(\:\partial\:\)) for granting or denying access. A weighted assessment of past access grants, data sensitivity, unauthorized users, request context, and historical access trends are considered. This complete study can make healthcare systems supported by IoT secure and flexible ACM, enabling informed decision-making. Based on this, a decision is made for the defendable access control, shown in Eq. (5).
$$\:\partial\:=\left.\begin{array}{c}\sum\:_{{\varnothing}}\left({f}_{d}*{d}^{{\prime\:}}\right)+{u}_{n}*\left(\frac{\raisebox{1ex}{${c}_{r}$}\!\left/\:\!\raisebox{-1ex}{${g}_{r}$}\right.}{\left(\gamma\:+R\right)}\right)+{k}_{h},\:Access\:grant\\\:\left(\frac{\prod\:_{{s}_{m}}{p}^{t}}{{k}_{h}+{k}_{0}}\right)*\left(Y+\alpha\:\right)+\sum\:_{{t}^{{\prime\:}}}\left({d}^{{\prime\:}}*{t}^{{\prime\:}}\right),\:Revoke\end{array}\right\}$$
(5)
The classification is performed for the varying services and determines the authorization. The authorization is given to the patients to handle the service and examine the anonymous entries and data download. The computation is based on the delegation, and the defendable service is forwarded to the end-users. This processing leads to access control and recommends\(\:\:R\) for the training data to improve the access rate. The above equation differentiates the access grant and revokes the operation for the relevant service forwarding. The first derivation indicates the access grant for the data analysis equated in Eq. (1). In this approach, the recommendation is performed for the access grant to the number of users, and it is represented as \(\:\:\left(\frac{\raisebox{1ex}{${c}_{r}$}\!\left/\:\!\raisebox{-1ex}{${g}_{r}$}\right.}{\left(\gamma\:+R\right)}\right)\). Here, both the assessment \(\:{s}_{m}\) and augmentation is centralized in this IoT environment.
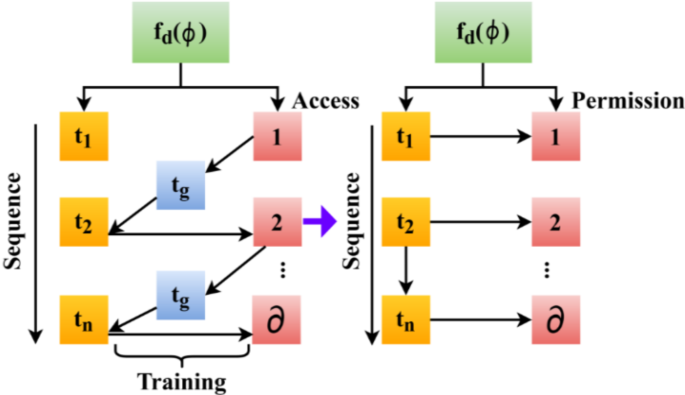
RF classification illustration.
The second derivation represents the revoke; if any unwanted access alert is examined in IoT infrastructure, the revoke operation is performed. It is executed if an access denial occurs during the time-of-service request and forwarding. In this approach, the security level is maintained for the patients and the blockchain for the augmentation\(\:\:{k}_{0}\). In this case, the authorization is balanced for the varying users, estimates the matching with the previous state, and provides the result on time. Figure 4 presents the classification illustration.
Sequential time observations are recorded for different access intervals in the permission-granting sequence. This sequence is observed for different classification instances for providing permission. The training is performed to verify the sequential access/grant for the users through classification (refer to Fig. 4). Thus, the classification model is performed in this RF method for the access grant and revokes, denoted as\(\:\:\partial\:\). Equation (6) performs the training data to enhance the detection of anonymous entries and data downloads.
$$\:\alpha\:\left({t}_{g}\right)=\left\{\begin{array}{c}\left(\frac{{e}_{0}}{\prod\:_{{r}_{d}}\left(R{*}d{\prime\:}\right)}\right)+\left(\left({k}_{h}{*}t{\prime\:}\right)+\left({w}_{0}*d{\prime\:}\right)\right)-{r}_{0}\\\:{d}^{{\prime\:}}=\left({u}_{0}+{m}_{i}\right)*{s}_{m}\\\:{s}_{m}=\left({e}_{0}+{o}_{n}\right)*\left({k}_{h}+{f}_{d}\right)\\\:{f}_{d}=\left(Y+{w}_{0}\right)*{q}_{e}\end{array}\right.$$
(6)
The training data is done by performing matching that deploys the blockchain for reliable security. Here, security determines the service forwarding and performs the recommendation.
The error data determines a better prediction model and determines the access granted to the users. The access is granted to the appropriate user by deploying the access control. The access control states the augmentation and assessment for a reliable result. The evaluation is carried out for the different service handling and provides the access grant to the relevant users. The previous state defines the training data \(\:{t}_{g}\) for the different sets of services, and it is represented as\(\:{\:r}_{0}\). Thus, the training data determines the authorization for the service handling and provides security. The prediction is evaluated based on the RF classification and deploys the concord patient/user-related service. In Table 2, the failure % for different user requests is tabulated.
Failure is computed for different granted requests, regardless of their pending status. In this case, the failure is estimated \(\:\partial\:\) using the training data.
Blockchain for access control mechanism
With blockchain technology, there is no longer any need to depend on a single authority for access control, as it offers a decentralized structure that eliminates this danger. Data integrity is ensured by the immutability of access control choices and procedures stored on the blockchain. The complete auditability and traceability of all transactions (access demand, authorization, refusal) are recorded on the blockchain. It is difficult for unauthorized individuals to manipulate access control since blockchain employs sophisticated encryption methods to secure data. At first, blockchain compiles information about access requests, such as the user’s role, the data type requested, the time of access, the location, the security of the device, and access trends of the past. With the use of access control history data, an RF model can be trained. Each data point comes with the above attributes and the matching access decision. Extract the pertinent features and feed them into the trained RF model whenever a new access request is submitted. The model can determine if the access request should be approved or denied by analysing the features provided. Ensure everyone can see the model’s reasoning and choice on the blockchain. An intelligent contract on the blockchain enforces the decision to give or refuse access.
Utilizing blockchain technology, the system oversees the granting of access. Access grants can be revoked and determined from blockchain records based on earlier access and delegation sequences. When deciding on a blockchain, the service in charge of deployment evaluates and enhances the end-user access policies. Assessing the demand and utilizing the blockchain for security are both done here. Security is the decision-making process followed by defendable access control and deployable blockchain. To further guarantee security, blockchain also suggests analyzing the training stage of data processing for this scheme and looking at the access-level security of the blockchain recommendation. Various services and extensive data exchange are compatible with the current security configuration.
Every node in the network is vital in an OACS or other blockchain-based access control system because it manages state transitions associated with user permissions and access requests. Common tasks include representing states, transitioning between states, verifying user credentials against stored states, determining whether access should be provided based on current permissions and delegation history, and updating the state to reflect changes in permissions.
In the consensus mechanism, nodes talk to each other until they agree on the status of the current permissions. That way, nobody can alter the record of user permissions without authorization, and all the nodes will have the same record. Every time someone asks for access and the blockchain decides to approve or deny that request, it’s recorded as a transaction. As a result, an auditable, immutable log is created.
The OACS class creates a blockchain for access requests and an index for user permissions. Request Access checks a user’s blockchain delegation history for validity. It considers the user’s credentials and past behaviour to determine resource access. If so, it grants or forbids access. Grant Access and deny Access record every choice as a blockchain transaction.

Pseudocode of blockchain-based access control.
The training is based on previous blockchain information and prediction; prediction is discussed in the following section.
Security prediction
The security prediction is performed based on matching the previous state and provides a reliable result. Here, the recommendation is made for the blockchain to ensure security. The permission is forwarded concerning the relevant information handling to the end-user in IoT. The utilization of the recent IoT for ubiquitous and concord patients is examined in the healthcare industry. Access-level security is determined to grant permission to access the services. Concerning this prediction, the upcoming anonymous entries are avoided, and the efficient access rate is explored. Equation (7) is used to predict the varying services, and here, matching is done with the previous state.
$$\:P=\left(\frac{S*H}{\raisebox{1ex}{$\left({w}_{0}+{k}_{h}\right)$}\!\left/\:\!\raisebox{-1ex}{${g}_{r}$}\right.}\right)+{\prod\:}_{d{\prime\:}}^{{l}_{a}}\left({r}_{d}*{\varnothing}\right)+\left(\left(\frac{{k}_{0}-R}{{c}_{r}}\right)*\left({f}_{d}-{e}_{n}\right)\right)-{r}_{0}$$
(7)
The prediction is performed by examining the service’s current and previous state in the healthcare industry. Here, the evaluation is done by deploying the defendable access control and providing permission for the delegate services.
The end-user requests the particular services, so the healthcare industry performs the mapping. This mapping matches the current and previous data states and forwards the relevant data to the end user. In this stage, the recommendation is made for access control and augmentation, and it is formulated as \(\:\left(\left(\frac{{k}_{0}-R}{{c}_{r}}\right)*\left({f}_{d}-{e}_{n}\right)\right)\). Here, the defendable process examines the security between the users and the devices. The analysis of anonymous entries and data downloads states the permission provided to the user. The computation time is included to perform the particular task and, from this prediction, is examined, and it is denoted as\(\:\:P\). The delegation scheme deploys interrupt-free healthcare record access, as shown in Eq. (8).
$$\:\gamma\:\left({d}^{{\prime\:}}\right)=\left({j}_{c}{*}{e}_{0}\right)+\left(\left(\frac{\sum\:_{{m}_{i}}\left({u}_{0}+t{\prime\:}\right)}{H+{q}_{e}}\right){*}{k}_{h}\right)+\left({k}_{0}{*}{s}_{m}\right)+{o}_{n}\left(\gamma\:\right)$$
(8)
In Eq. (8), the interrupt-free healthcare record access determines the access grant for the end users. The evaluation is carried out for the varying service handling, examines the augmentation and assessment, and deploys the delegated. The previous state performs the matching, and from this approach, permission is granted to revoke the services. Here, the recommendation is made to provide access control and deploy the defendable access control. The evaluation is done by deploying the access to the end user and determining the blockchain record based on the previous state and delegation sequences. The access control is forwarded to the secure user in the network and balances the security for the access level.
The analysis is done by determining the delegation scheme, examining the access control, and providing the authorization, and it is denoted as\(\:{\:j}_{c}\). The data forwarding is done securely in the centralized IoT augmentation and assessment, providing post-to-healthcare record access. The evaluation is done by deploying the permission to the repository and estimating the reliable processing for the delegation scheme. This delegation scheme includes the augmentation and assessment for healthcare record access in IoT. Thus, authorization is performed for the varying services in the environment. In this evaluation, the interrupt-free healthcare record access is determined, and from this blockchain, the recommendation is formulated in Eq. (9).
$$\:{k}_{h}\left(R\right)=\left({c}_{r}+t{\prime\:}\right)*\left(\frac{H*{e}_{n}}{\sum\:_{{g}_{r}}\left({d}^{{\prime\:}}+{e}_{0}\right)}\right)+\left({q}_{e}\left({m}_{i}\right)*{o}_{n}\right)+\left(\frac{{j}_{c}+{w}_{0}}{\raisebox{1ex}{$\partial\:$}\!\left/\:\!\raisebox{-1ex}{$S$}\right.}\right)$$
(9)
The blockchain recommendation analyzes this scheme’s training state of data processing using Eq. (6). The performance is used to state the authorization of service forwarding from one state to another. Figure 5 presents the recommendation process.
Blockchain recommendation process.
The recommendation process relies on matching updates after the request processing. In this process, the classified intervals are used for decision-making. Blockchain records are used for information updates and access to information storage. This is replicated in the services provided by the healthcare industry for retaining service-level security (refer to Fig. 5). In the healthcare industry, computation leads to examining the security and balances throughout the iteration steps. In the IoT healthcare industry, service delegation is performed to determine the security and access grant. The access grant to the user states the augmentation and assessment. It is a pre-defined term that holds the number of user access, and from this, the service is forwarded to the appropriate user by matching. From this, forwarding is done based on the classification method, and it is represented as\(~\left( {\frac{{j_{c} + w_{0} }}{{\partial /S}}} \right)\). The determination of access and denial is formulated in Eq. (10), which examines Eq. (5), which indicates the classification model.
$$\emptyset \left( {S,n^{\prime } } \right) = \left\{ {\begin{array}{*{20}l} {\left( {Y + q_{e} } \right)*\mathop \sum \limits_{{r_{0} }} \left( {e_{0} + w_{0} } \right) + \left( {\frac{{e_{0} – f^{\prime } /v_{k} }}{{k_{h} }}} \right)} \hfill \\ {f^{\prime } = \left( {l_{a} {\text{*}}c_{r} } \right) + r_{0} } \hfill \\ {r_{0} = P + \left( {\Delta \left( {c^{\prime } } \right){\text{*}}m_{i} } \right)} \hfill \\ {m_{i} = r_{0} \left( {e_{0} } \right)*t^{\prime } + w_{0} } \hfill \\ \end{array} } \right.$$
(10)
The determination is carried out for the access and denial in service forwarding. From this approach, blockchain is used to define user permission. Concerning user permission, anonymous entries and data downloads are used to state the security. The security of the user and the devices in IoT is balanced. Here, the computation matches the current and the previous state and provides the result. The derivation is performed based on the user’s requirement and grants access on time. The access control and granting permission to use the service is termed from the authorization. The service authorization leads to examining the augmentation and assessment of the upcoming data handling in the healthcare centre. Table 3 presents the request examination for different delegation factors.
The examination factor is high if the matching is high, whereas complexity is less. If the matching is high, it reduces the denial ratio, and hence the examination is high. The examinations are performed based on\(\:\:P\) and interrupt free access delegations. Therefore, the access rate is high, reducing the denial, as shown in Table 3.
Access and denial are performed concerning the failure in the process, and it is termed as\(\:\:f{\prime\:}\). The denial is made by determining the matching process with the requirement and defining the delegation for access control. The prediction is made by determining the previous state of action and deploying the revoke and access grant. The access grant is used to state the matching\(\:\:\varDelta\:\:\)and decrease the denial of service, and it is denoted as\(\:\:n{\prime\:}\). Thus, determining access control and denial is performed by decreasing the failure in networking healthcare data transmission. Equation (11) evaluates the access rate and shows better improvement.
$$\:\beta\:={k}_{h}\left(Y\right)*\left(\partial\:+\frac{{l}_{a}}{{o}_{n}}\right)+\left({e}_{n}+{u}_{n}\right){q}_{e}-{r}_{0}$$
(11)
The access rate is enhanced in this approach by decreasing the failure and defining the defendable access control scheme. The delegation of service determines the authorization by concerning the service to the requested user on time. The computation time is reduced in this processing, and permission is provided to secure users from this state. The security level is maintained for the varying users and the services based on the requirement, and it is equated as\(\:\:\left({e}_{n}+{u}_{n}\right){q}_{e}\). The evaluation\(\:\:\beta\:\) is done to prevent anonymous entry into IoT and access to improper records. The matching process is derived in Eq. (12), which indicates the prediction model for the current and previous processing state.
$$\:\varDelta\:={d}^{{\prime\:}}\left({e}_{0}\right)*\left({f}_{d}+\frac{S*{l}_{a}}{{t}_{g}}\right)+\left(\sum\:\left({v}_{k}*{c}^{{\prime\:}}\right)-{r}_{0}\right)+P$$
(12)
The matching is performed with the previous access and delegation sequences for the number of services. The evaluation is used to deploy the anonymous detection and provides the evaluation for the access control. The access control determines the dependable services and provides the recommendation process. The recommendation defines the permission for the current and the previous state and provides the result based on the matching. For every computation step, matching examines the defendable access control. In this case, the access grant and revoke are used to determine the blockchain for security. Equation (13) performs access-level security to decrease the false rate.
$$\:S\left(\alpha\:\right)=\frac{1}{{u}_{n}+{e}_{n}}*{q}_{e}\left(\left({w}_{0}+{u}_{0}\right)+{t}_{g}*\left(P+\varDelta\:\right)\right)+{g}_{r}\left({e}_{0}+H\left({u}_{0}\right)\right)$$
(13)
The above equation explores access-level security in the blockchain recommendation to ensure security. The security level is balanced for the varying services and ubiquitous information sharing. The defendable access control determines the augmentation and assessment. The computation deploys the authorized access level to the secure user to maintain the related service forwarding. In this state, the false rate decreases for the varying services users request. It is achieved using an OACS and RF classification to address the issues and ensure security. Machine learning deploys training data in the IoT-based healthcare industry and transmits relevant services to patients with less computation time.
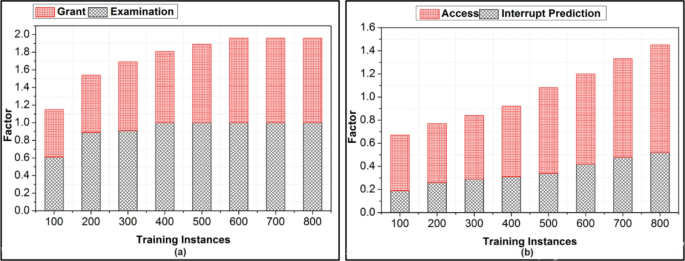
(a) Grant and examination factor analysis (b) Access and interrupt factor analysis.
Figure 6a analyzes the access grant and request examination factors under different training instances. As the training instances vary, the learning is instigated based on classification. This identifies the grant and revokes cases for requests in the succeeding intervals. Therefore, the examination is performed for previous intervals and stored in the blockchain for further delegation. This improves the access rate for the examined requests, preventing interruptions. Based on the stored information, the interrupt-causing requests are identified. The identified users are denied new service provisioning, and the current requests are revoked. This ensures secure and liable healthcare data sharing between the devices under different training instances, as shown in Fig. 6b.