The recent change in Healthcare/UHC data breaches have exposed serious healthcare vulnerabilities, including outdated systems and weak security measures. In response, the Global IT Research and Advisory Firm Info-Tech Research Group is launching new insights and offering a cybersecurity strategy to help healthcare organizations defend against evolving threats. In the resource, Info-Tech highlights the urgent need to improve cybersecurity practices, providing key strategies for security leaders to mitigate ransomware risk, enhance data protection, and enhance incident response capabilities.
Toronto, March 13, 2025 /PRNewswire/-2024 Change Healthcare/UHC Data Breach highlighted the urgent need to enhance cybersecurity within the healthcare sector. This violation, which uncovered sensitive patient records and disrupted hospital operations, highlighted significant vulnerabilities, particularly with a growing reliance on third-party vendors and outdated IT disaster recovery plans. To help security leaders step up their defenses and take proactive steps to protect patient care in the aftermath of a cyber incident, Info-Tech Research Group has published their learned blueprint lessons and life after healthcare institutions.
“In today's healthcare landscape, organizations face an increasing number of cybersecurity challenges due to their reliance on third-party vendors and complex IT environments,” said Sharon Auma-Ebanyat, research director at Info-Tech Research Group. “The biggest healthcare violations, including Change Healthcare/UHC, highlighted serious vulnerabilities, disruption to hospital operations, claims and patient records exposure, which underscore the urgent need for a comprehensive strategy to address these risks.”
The company reports that despite the escalation of the cyber threat landscape, many healthcare organizations have yet to fully implement multifactor authentication, particularly for remote access services, which expose critical systems to attackers who exploit stolen qualifications.
Info-Tech insights highlight the challenges posed by interconnected IT environments, making it difficult for organizations to detect and address security gaps.
“Many healthcare providers encounter obstacles such as virtual and digital connectivity, limited budgets and resources, and outdated IT disaster recovery plans that cannot address complex, interconnected systems that make it difficult to identify and fix vulnerabilities,” adds Auma-Ebanyat. “Traditional disaster recovery approaches overlook third-party risks and the evolving nature of virtual environments, increasing their sensitivity to cyberattacks.”
Info-Tech advises the need for a more comprehensive and proactive cybersecurity approach to mitigate these risks.
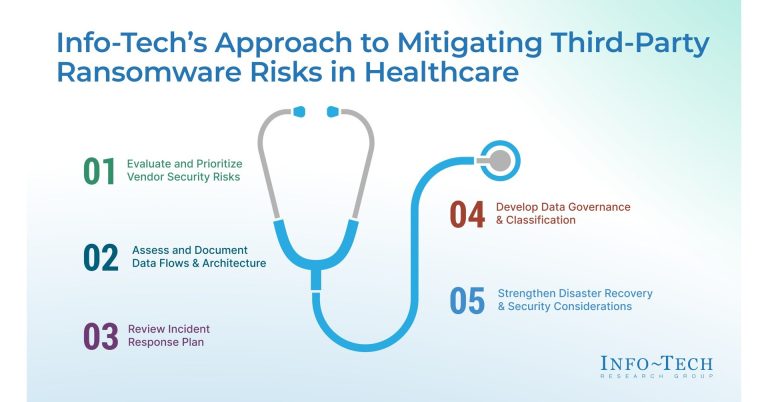
A 5-step approach to mitigating third-party ransomware risk
In the recently published resource lessons and life learned after the healthcare organization's violations, Info-Tech offers a structured five-step approach to help healthcare in mitigating third-party ransomware risks.
The five-stage approach includes:
Assess and prioritizes vendor security risks
Healthcare organizations should assess vendor security risks and prioritize high-risk partners, especially those processing sensitive patient data. Dual-vendor strategies for SaaS applications reduce dependency on a single provider and improve resilience to disruption. Evaluate and document data flows and architectures
Mapping data flows help identify vulnerabilities and potential ransomware entry points. Strengthening network segmentation and containment strategies minimize damage and prevent the spread of attacks. Check and strengthen incident response plans
Regularly updating incident response plans will help your organization respond quickly to ransomware threats. Tabletop exercises help teams test their response strategies and improve adjustments during actual incidents. Develop data governance and classification
A powerful data governance framework categorizes and protects sensitive data. Implementing access control and encryption provides greater security and reduces exposure to ransomware threats. Improve disaster recovery and security considerations
Robust data backup and redundant systems allow critical operations to continue during an attack. Improved authentication, encryption, and access controls further minimize the impact of violations.
“This study provides a roadmap to mitigate the risk of third-party ransomware and data breaches. Insights on current healthcare cybersecurity threats, lessons learned from change healthcare/UHC data breaches, and strategies to prevent future incidents.”
By leveraging insights from Info-Tech's blueprints, healthcare organizations can take critical steps to strengthen their cybersecurity strategies and disaster recovery plans. Expert-led recommendations outlined in data-backed resources help security leaders protect sensitive patient data, maintain operational resilience, and prepare for evolving cyber threats.
For exclusive and timely commentary from medical field expert Sharon Auma-Ebanyat, as well as complete lessons learned and access to life after violating the medical institution blueprint, please contact us (Email protection).
About Info-Tech Research Group
Info-Tech Research Group is one of the world's leading research and advisory companies, proudly serving over 30,000 IT and HR professionals. The company produces fair and highly relevant research and provides advisory services to help leaders make strategic, timely and informed decisions. For nearly 30 years, Info-Tech has partnered closely with our teams to provide everything they need, from actionable tools to analyst guidance, ensuring that organizations have measurable results.
For more information about the Info-Tech department, see McLean & Company. Buy HR Research and Advisory Services, Software Insights.
Media experts can register for unlimited access to research through IT, HR, software, and hundreds of industry analysts through the company's Media Insider Program. Please contact us to access (Email protection).
For more information about the Info-Tech Research Group, visit infotech.com and connect via LinkedIn and X to access the latest research.
Source Information Tech Research Group